As the world’s leading content management system, WordPress powers millions of websites, making it a prime target for cyber threats. Protect your digital presence by staying informed and proactive—because every click counts in securing your online legacy!
Cybersecurity Threats That Target WordPress Sites
In our increasingly digital world, where words and ideas flow freely through the vast expanse of the internet, the power of a well-crafted website cannot be underestimated. For millions of individuals and businesses, WordPress stands as the cornerstone of their online presence, offering a platform that is as user-friendly as it is versatile. However, with great opportunity comes great risk. As the popularity of WordPress continues to soar, so too do the cybersecurity threats that lurk in the shadows, poised to compromise the integrity of your site and the trust of your audience.
Imagine pouring your heart into creating a vibrant online community, only to have it jeopardized by malicious attacks that can dismantle everything you’ve built in seconds. This article seeks to illuminate the pressing cybersecurity threats specifically targeting WordPress sites, empowering you with the knowledge to fortify your digital fortress. Together, we will explore the landscape of vulnerabilities that exist, the motives behind these nefarious attacks, and the proactive measures you can take to safeguard your passion project. Embrace the challenge; let’s turn the tide in the battle for security, ensuring your WordPress site not only survives but thrives in the face of adversity.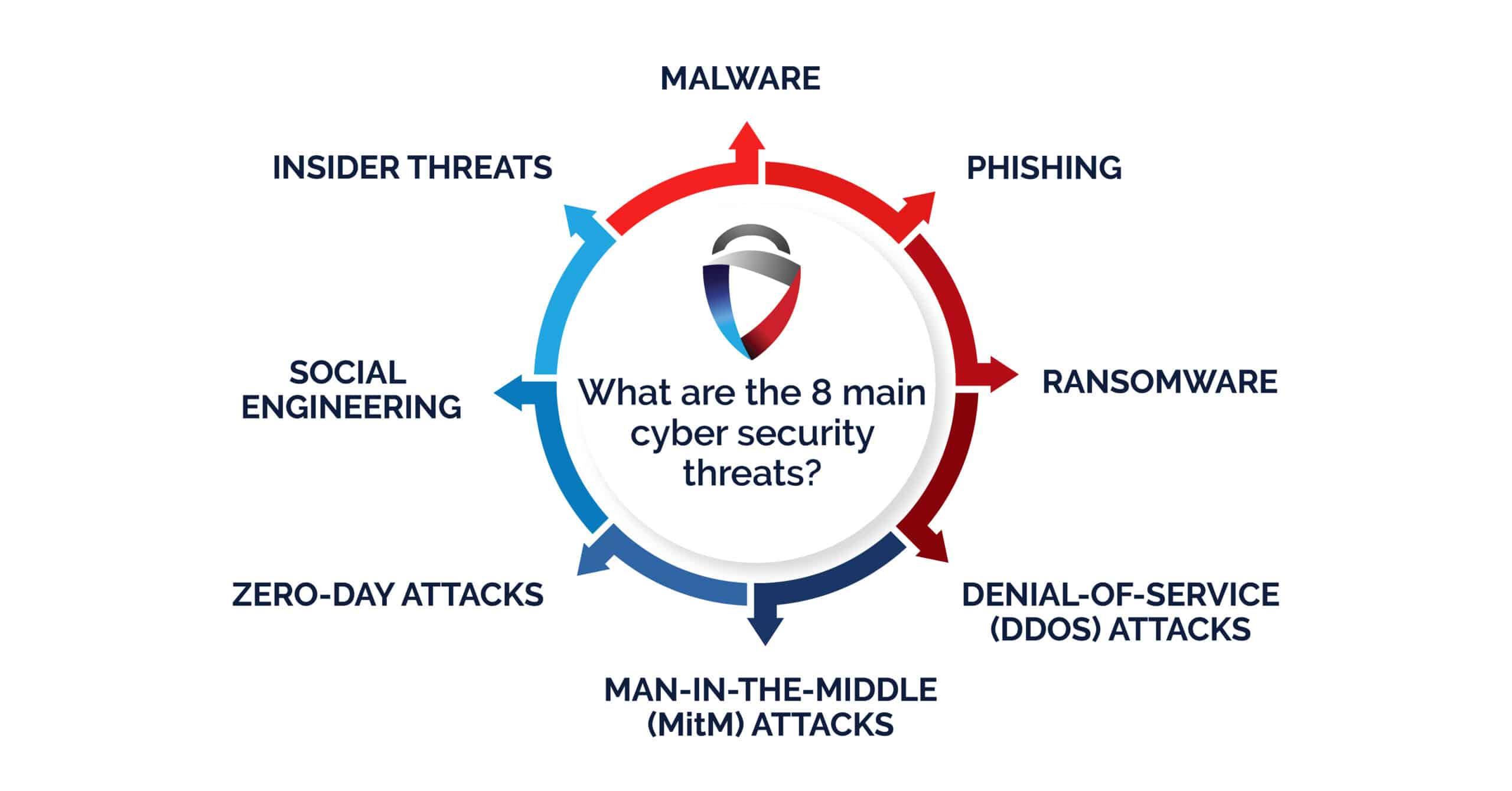
Understanding the Landscape of Cybersecurity Threats to WordPress Sites
The digital realm is fraught with challenges, and WordPress sites, being a popular choice for millions, are often the primary targets for cybercriminals. Understanding the various threats that loom over these platforms is paramount to safeguarding your online presence. Here are some of the most prevalent cybersecurity threats you should be aware of:
- Malware Attacks: Malicious software can infiltrate your site, leading to data breaches, defacing your website, or even redirecting visitors to harmful sites.
- SQL Injection: This technique allows attackers to manipulate your database through vulnerable input fields, potentially gaining unauthorized access to sensitive information.
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into your site, which can compromise user data and lead to identity theft.
- Brute Force Attacks: Cybercriminals use automated tools to guess your login credentials, aiming to gain unauthorized access to your admin area.
- Phishing Attacks: These deceptive tactics trick users into providing personal information through fake login pages or emails, which can be detrimental to both site owners and users.
To further illustrate the landscape of these threats, consider the following table that highlights the potential impacts of each type of attack:
| Type of Attack | Potential Impact | Recommended Action |
|---|---|---|
| Malware Attacks | Data breaches and site defacement | Regularly scan and update your site |
| SQL Injection | Unauthorized data access | Use parameterized queries and security plugins |
| XSS | Data theft | Implement input validation |
| Brute Force Attacks | Admin access gain | Limit login attempts and use strong passwords |
| Phishing Attacks | Identity theft | Educate users about recognizing phishing attempts |
As you navigate the complexities of securing your WordPress site, remember that staying informed is your first line of defense. Regular updates, security plugins, and proactive monitoring are essential components of a robust cybersecurity strategy. By understanding the potential threats and how they manifest, you empower yourself to take effective action against them.
In this ever-evolving landscape, adapting to new threats is crucial. Cybersecurity is not merely about reacting after an incident occurs; it’s about creating a resilient environment that anticipates and mitigates risks. Make it a priority to educate yourself and your team about best practices and emerging threats. This commitment not only protects your site but also fosters trust with your users.

Common Vulnerabilities That Put Your WordPress Site at Risk
WordPress is one of the most popular content management systems worldwide, but its widespread use makes it a prime target for cybercriminals. Understanding the common vulnerabilities that can jeopardize your site is essential for every WordPress administrator. Here’s a closer look at some key risks:
- Outdated Plugins and Themes: Many website owners neglect to update their plugins and themes, leaving their sites exposed to security loopholes. Cyber attackers often exploit these outdated components to gain unauthorized access.
- Weak Passwords: The use of simple or common passwords is a recipe for disaster. Implementing strong password policies can greatly reduce the risk of brute force attacks.
- Insecure Hosting Environment: Not all hosting providers offer the same level of security. Choosing a provider that prioritizes cybersecurity can make a significant difference.
- Unprotected Admin Area: The default login URL for WordPress can be easily guessed. Securing your wp-admin area with measures like two-factor authentication (2FA) can add an extra layer of protection.
- SQL Injection Vulnerabilities: Attackers often exploit vulnerabilities in your database queries. Ensuring that your website uses secure coding practices can help mitigate this risk.
To illustrate the impact of these vulnerabilities, consider the following table, which outlines potential consequences based on the type of security flaw:
| Vulnerability Type | Potential Consequence |
|---|---|
| Outdated Plugins | Site Hack or Data Breach |
| Weak Passwords | Unauthorized Access |
| Insecure Hosting | Downtime or Data Loss |
| SQL Injection | Data Theft |
In addition to understanding these vulnerabilities, proactive measures can substantially lessen the impact of potential threats. Regular security audits, timely updates, and robust backup strategies are fundamental practices for maintaining the integrity and security of your WordPress site.
Furthermore, educating all users who have access to your site about the importance of cybersecurity can create a culture of caution. An engaged and informed user base is your first line of defense against cyber threats.

The Rising Tide of Malware Attacks Targeting WordPress Platforms
The landscape of cybersecurity is constantly evolving, and with it, the threats targeting WordPress platforms are becoming increasingly sophisticated. As one of the most popular content management systems globally, WordPress is a prime target for cybercriminals looking to exploit vulnerabilities. The rise in malware attacks has made it crucial for website owners to stay informed and proactive in safeguarding their sites.
Recent statistics reveal a startling increase in malware infiltration attempts, with a particular focus on the following:
- Brute Force Attacks: Attackers use automated scripts to guess passwords at an alarming rate.
- Malicious Plugins: Unverified plugins can introduce vulnerabilities that open the door to malware.
- SQL Injection: Exploiting database vulnerabilities allows attackers to manipulate and extract sensitive information.
Understanding the motivations behind these attacks is essential for developing robust defenses. Cybercriminals often aim to:
- Steal Data: Personal and financial information can be sold on the dark web.
- Disrupt Services: DDoS attacks can render websites inoperable, leading to reputational damage.
- Distribute Malware: Infecting visitors’ devices to expand their network of compromised machines.
To combat this rising tide of threats, website owners must implement a multi-layered security strategy. Key components should include:
- Regular Updates: Keeping WordPress core, themes, and plugins updated to patch vulnerabilities.
- Strong Password Policies: Enforcing complex passwords and two-factor authentication.
- Security Plugins: Utilizing comprehensive security solutions to monitor and mitigate risks.
Here’s a quick look at some essential security plugins that can enhance your WordPress site’s defenses:
| Plugin Name | Features |
|---|---|
| Wordfence Security | Firewall, malware scanner, and login security. |
| iThemes Security | Brute force protection and file change detection. |
| Sucuri Security | Website malware scanner and security activity auditing. |
as the threats targeting WordPress platforms continue to rise, it is imperative for website owners to prioritize their cybersecurity measures. By staying vigilant and employing best practices, you can protect not only your site but also the sensitive data of your users. The power to secure your WordPress platform lies in your hands—take action today!
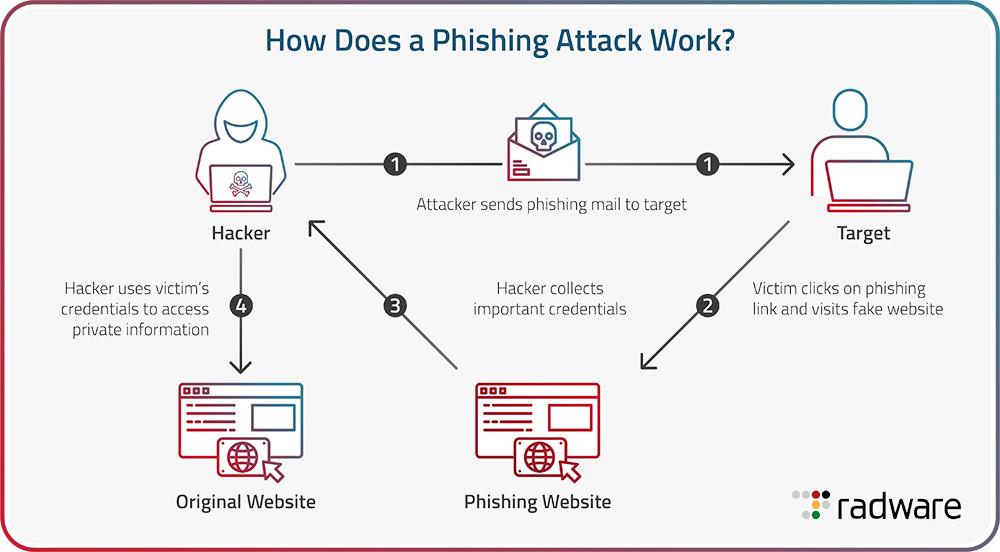
Phishing Attacks: How Cybercriminals Manipulate WordPress Users
Phishing attacks are one of the most insidious threats that WordPress users face today. Cybercriminals employ various tactics to manipulate unsuspecting users, often disguising themselves as legitimate entities. Understanding their methods is crucial in safeguarding your website and personal information.
One common tactic is the use of spoofed emails. Cybercriminals craft messages that appear to come from trusted sources, such as a hosting provider or WordPress itself. These emails often contain urgent requests, enticing users to click on malicious links or download harmful attachments. Here are some signs to look out for:
- Generic Greetings: Phishing emails often lack personalization.
- Urgent Language: Scare tactics to prompt immediate action.
- Suspicious Links: Hovering over links reveals mismatched URLs.
Another prevalent method is phishing websites that mirror legitimate WordPress login pages. Users may be tricked into entering their credentials, which are then captured by the attackers. These fraudulent sites can be remarkably convincing, often using the same branding and layout as the original. To avoid falling victim:
- Check the URL: Always verify the website address before logging in.
- Look for HTTPS: Ensure there’s a secure connection.
- Enable Two-Factor Authentication: Adding an extra layer of security can deter attackers.
Moreover, cybercriminals can exploit plugins and themes. By sending targeted phishing emails claiming there’s a critical update required for a plugin, they can trick users into installing malicious software. This emphasizes the need for:
- Regular Updates: Keep your WordPress installations current.
- Trusted Sources: Only download plugins and themes from reputable developers.
To better illustrate the impact of phishing attacks on WordPress users, consider the following table:
| Phishing Method | Impact |
|---|---|
| Spoofed Emails | Credential Theft |
| Fake Login Pages | Account Compromise |
| Malicious Plugin Updates | Site Vulnerability |
By recognizing these tactics and implementing robust security measures, you can significantly reduce the risk of falling victim to phishing attacks. Stay vigilant, educate your team, and create a culture of cybersecurity awareness within your organization.

The Importance of Regular Updates for WordPress Security
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is not just advisable; it’s essential. For WordPress site owners, regularly updating your core software, themes, and plugins is a critical line of defense against malicious attacks. Here’s why prioritizing updates should be at the forefront of your website security strategy:
- Vulnerability Patching: Each update often includes patches for newly discovered vulnerabilities. By neglecting these updates, you leave your site exposed to exploits that cybercriminals actively seek out.
- Enhanced Functionality: Regular updates not only bolster security but also introduce new features and improvements. This can enhance user experience and increase engagement on your site.
- Compatibility Checks: As WordPress evolves, so do its themes and plugins. Regular updates ensure that your website remains compatible across the board, preventing conflicts that could compromise security.
- Reduction in Downtime: Outdated software can lead to performance issues and crashes. Keeping your site updated minimizes the risk of downtime, which can have a direct impact on your reputation and revenue.
To illustrate how timely updates can impact the security of your WordPress site, consider the following table that outlines common vulnerabilities and their corresponding updates:
| Vulnerability | Potential Impact | Recommended Action |
|---|---|---|
| Outdated Plugins | Site compromise, data breaches | Update to latest version |
| Core WordPress Version | Increased risk of hacking | Update immediately |
| Discontinued Themes | Security loopholes | Switch to supported themes |
Moreover, it’s important to adopt a proactive approach to updates. Consider setting a schedule for checking and applying updates regularly. This not only ensures that your site remains secure but also fosters peace of mind. You might even consider leveraging automated updates, which can streamline the process significantly.
the importance of regular updates for your WordPress site cannot be overstated. Each update is a step toward safeguarding your digital presence against the onslaught of cyber threats. By committing to this practice, you are not just protecting your website; you are investing in the trust and safety of every visitor that steps through your online doors.
Strengthening Your Defense Against Brute Force Attacks
In the ever-evolving landscape of cybersecurity threats, brute force attacks remain a persistent menace for WordPress site owners. These attacks, where malicious actors attempt to gain unauthorized access by systematically guessing passwords, can be thwarted through a series of proactive measures. By strengthening your defenses, you not only protect your site but also build a robust foundation for your digital presence.
To effectively counter brute force attempts, consider implementing the following strategies:
- Strong Password Policy: Encourage the use of complex passwords that include a mix of uppercase letters, lowercase letters, numbers, and special characters. Eliminating easily guessable passwords is crucial.
- Limit Login Attempts: Use plugins or server settings to restrict the number of login attempts from a single IP address. This measure can significantly reduce the chances of successful brute force attacks.
- Two-Factor Authentication (2FA): Require an additional layer of security by implementing 2FA for all users. This step requires users to verify their identity through a secondary method, making unauthorized access exceedingly difficult.
- Change the Default Username: Avoid using the default “admin” username, as it is a common target for attackers. Create unique usernames that are less predictable.
In addition to these preventive measures, consider regular monitoring and security audits. Keeping your WordPress core, themes, and plugins updated not only enhances functionality but also fortifies your site against vulnerabilities that could be exploited in brute force attacks.
Here’s a simple overview of some effective tools and plugins that can assist you in fortifying your defenses:
| Tool/Plugin | Functionality |
|---|---|
| Wordfence | Firewall and malware scanner with login security features. |
| iThemes Security | Comprehensive security plugin that offers login protection and more. |
| Limit Login Attempts Reloaded | Limits login attempts to prevent brute force attacks. |
| Google Authenticator | Enables two-factor authentication for an extra layer of security. |
By taking proactive steps to strengthen your defense against brute force attacks, you empower yourself and your users with confidence. Remember, the cost of prevention is always less than the cost of a breach. Start implementing these strategies today to safeguard your WordPress site against potential threats.
Implementing Strong Password Policies for Enhanced Security
In the burgeoning landscape of cybersecurity, especially for WordPress sites, the strength of your password policy can make all the difference. Weak passwords are a common gateway for cybercriminals, making it essential for website administrators to implement robust strategies. By fostering a culture of strong password usage, you empower your team and safeguard your digital assets.
One effective way to enhance your password policy is to incorporate the following principles:
- Length Over Complexity: Encourage passwords that are at least 12–16 characters long, combining letters, numbers, and symbols.
- Regular Updates: Set mandatory password changes every 3–6 months to mitigate risks from potential breaches.
- Prohibit Common Passwords: Maintain a blacklist of commonly used passwords to prevent users from selecting easily guessable options.
- Two-Factor Authentication (2FA): Implement 2FA to add an additional layer of security beyond just passwords.
Additionally, adopting a password management tool can significantly enhance your security strategy. These tools can generate, store, and autofill complex passwords, ensuring that users don’t rely on memory for their login credentials. By integrating these password managers, you not only simplify the login process but also promote strong, unique passwords for each site.
Moreover, consider conducting regular training sessions for your team on password security. Awareness is key; educating users about the importance of strong passwords and the consequences of neglect can transform their habits. You can utilize resources like:
- Password strength meters
- Simulated phishing attacks
- Workshops on recognizing social engineering tactics
| Password Policy Aspect | Best Practice |
|---|---|
| Minimum Length | 12-16 Characters |
| Change Frequency | Every 3-6 Months |
| 2FA Implementation | Mandatory for All Users |
By taking these proactive steps, you can create a formidable defense against potential threats targeting your WordPress site. A commitment to strong password policies not only protects your site but also fosters a secure environment for your users. Let your strong passwords be the cornerstone of your cybersecurity strategy, empowering your digital presence with resilience against evolving threats.

Leveraging Security Plugins to Fortify Your WordPress Site
Key Features of Effective Security Plugins
When it comes to fortifying your WordPress site, the right security plugins can offer invaluable protection against a multitude of cyber threats. Here are some key features to look for:
- Firewall Protection: A robust firewall acts as a barrier between your site and potential attackers, blocking malicious traffic before it even reaches your server.
- Malware Scanning: Regular scans for malware help identify vulnerabilities early, allowing for timely remediation.
- Brute Force Attack Prevention: Prevent unauthorized access by limiting login attempts and implementing CAPTCHA challenges.
- Real-time Security Monitoring: Continuous monitoring alerts you immediately to suspicious activity, ensuring prompt action can be taken.
- Backup Solutions: Automatic backups can save your site in the event of a breach, allowing for a quick recovery.
Popular WordPress Security Plugins
Selecting the right plugin can make a significant difference in your site’s security posture. Below is a table showcasing some of the most popular security plugins along with their standout features:
| Plugin Name | Main Features |
|---|---|
| Wordfence | Firewall, malware scanning, live traffic monitoring |
| iThemes Security | Brute force protection, file change detection, two-factor authentication |
| Sucuri Security | Security activity auditing, remote malware scanning, blacklist monitoring |
| All In One WP Security | User account security, database backup, file integrity monitoring |
Implementing Security Best Practices
In addition to utilizing security plugins, adopting best practices is essential for maintaining a secure WordPress site. Consider the following strategies:
- Regular Updates: Keep your WordPress core, themes, and plugins up to date to mitigate potential vulnerabilities.
- Strong Passwords: Use complex passwords and change them periodically to reduce the risk of unauthorized access.
- User Role Management: Limit user capabilities by assigning appropriate roles, ensuring only trusted individuals have administrative access.
- SSL Certificates: Secure your site with HTTPS to encrypt data exchanged between users and your server.
Integrating Security Measures into Your Workflow
For optimal protection, integrate security measures into your regular workflow. Schedule regular security audits, maintain backups, and ensure that all security features of your chosen plugins are configured correctly. This proactive approach not only protects your site but also instills confidence in your visitors, demonstrating your commitment to their safety.
The Role of Web Hosting in Protecting Your WordPress Environment
In the digital landscape, where threats loom at every corner, the importance of choosing the right web hosting for your WordPress site cannot be overstated. Web hosting acts as the fortress that not only houses your site but also shields it from various cybersecurity threats. A robust hosting provider implements a range of security measures that can significantly reduce the risk of attacks.
When selecting a web host, consider the following key security features:
- Regular Backups: Ensure your host offers automated backups to safeguard your data against loss during unexpected breaches.
- SSL Certificates: A reliable provider will offer SSL encryption, which secures data exchange, providing an extra layer of protection for both you and your visitors.
- Firewall Protection: Look for hosts that integrate firewalls to filter out malicious traffic before it reaches your site.
- Malware Scanning: Regular scanning for vulnerabilities can help identify and mitigate potential threats proactively.
Moreover, hosting companies that specialize in WordPress often provide tailored solutions that cater specifically to WordPress vulnerabilities. These providers typically offer:
- Enhanced security protocols specifically designed for the WordPress architecture.
- One-click updates for WordPress core, themes, and plugins, ensuring that all components are current and less susceptible to exploitation.
- Support for plugins that further bolster security, such as firewalls and anti-spam tools.
| Feature | Importance |
|---|---|
| Automatic Backups | Prevents data loss |
| SSL Certificates | Secures user data |
| Firewall Protection | Blocks malicious traffic |
| Malware Scanning | Identifies vulnerabilities |
By investing in a hosting provider that prioritizes security, you not only protect your website but also enhance your credibility with visitors. Trust is a crucial currency in the online world, and when users see that your site is secure, they’re more likely to engage and convert. Moreover, a secure hosting environment allows you to focus on growing your online presence without the looming anxiety of a potential breach.
Ultimately, your web hosting choice can define the resilience of your WordPress site against cybersecurity threats. Make informed decisions, leverage the right features, and transform your website into a safe haven for both you and your visitors.

Backup Strategies That Ensure Business Continuity After an Attack
In the face of increasing cybersecurity threats targeting WordPress sites, it is imperative for businesses to implement robust backup strategies that not only protect data but also ensure seamless continuity in the event of an attack. A comprehensive backup plan is essential to mitigate the risks associated with data loss and to maintain operational integrity.
One of the most effective strategies is to adopt a multi-layered backup approach. This includes:
- Local Backups: Regularly create backups stored on local drives. This allows for quick recovery in case of immediate threats.
- Cloud Backups: Utilize cloud services that provide off-site storage, ensuring that your data is safe from local disasters or attacks.
- Incremental Backups: Schedule backups that only save changes made since the last backup, optimizing storage space and reducing backup times.
Another key aspect is the frequency of backups. Establishing a routine backup schedule is crucial. Consider implementing:
| Backup Type | Frequency | Recommended Tools |
|---|---|---|
| Daily Backups | Every 24 hours | UpdraftPlus, BackupBuddy |
| Weekly Backups | Every 7 days | VaultPress, Duplicator |
| Monthly Backups | Every 30 days | WP Time Capsule, BlogVault |
Moreover, ensuring the integrity and security of backups is paramount. Encrypt your backup data and store it in secure locations to prevent unauthorized access. Regularly test your backup restoration process to confirm that your data can be recovered swiftly and accurately. This proactive measure not only builds confidence but also prepares your team for a quick response in a crisis.
Lastly, consider integrating monitoring tools that alert you to unusual activity on your site. By combining regular backups with vigilant monitoring, you create a formidable defense against potential attacks. Remember, the goal is not only to recover after an incident but to stay one step ahead of cybercriminals.

Educating Your Team: Cybersecurity Awareness for WordPress Users
Understanding the Threat Landscape
In the ever-evolving digital landscape, WordPress users face a myriad of cybersecurity threats. It’s crucial for your team to recognize and understand these risks to create a secure online environment. Here are some of the most prevalent threats targeting WordPress sites:
- Malware Infections: Malicious software that can hijack your website, steal sensitive data, or even turn your site into a spam platform.
- Brute Force Attacks: Automated attempts to guess your login credentials, often targeting weak passwords.
- SQL Injection: A technique used by attackers to manipulate your database, potentially leading to data breaches.
- Cross-Site Scripting (XSS): A vulnerability that allows attackers to inject malicious scripts into webpages viewed by other users.
- Theft of Sensitive Data: Targeting customer information, payment details, or any proprietary data stored on your site.
Building a Cybersecurity Culture
Educating your team is the first line of defense against these threats. Fostering a culture of cybersecurity awareness can significantly reduce risks. Here are strategies to cultivate this mindset:
- Regular Training Sessions: Conduct consistent workshops focusing on the latest threats and best practices.
- Phishing Simulations: Run simulated phishing attacks to teach employees how to recognize fraudulent emails.
- Clear Protocols: Establish clearly defined protocols for reporting suspicious activity.
- Encouraging Strong Password Practices: Recommend the use of password managers and the implementation of multi-factor authentication.
Staying Ahead with Tools and Resources
Utilizing the right tools can empower your team to protect your WordPress site. Consider integrating these essential resources:
| Tool | Purpose |
|---|---|
| Wordfence | Firewall and malware scanner to protect your site. |
| Sucuri | Website security platform for monitoring and malware removal. |
| Jetpack | Offers security features including brute force protection and downtime monitoring. |
| iThemes Security | Enhances security with over 30 features aimed at securing and protecting your site. |
Empowering Your Team
By empowering your team with knowledge and tools, you cultivate a proactive approach to cybersecurity. Ensure that every member understands their role in maintaining security, from regular updates to identifying suspicious activities. Encourage open discussions about cybersecurity, and celebrate milestones achieved in secure operations.

Responding Effectively to a Security Breach on Your Site
When confronted with a security breach, the first step is to remain calm and composed. A panic-stricken response can lead to hasty decisions that may exacerbate the situation. Instead, focus on implementing a structured plan to mitigate the impact of the breach effectively.
Immediate Actions: Your initial response should involve a series of critical actions:
- Assess the Damage: Identify the extent of the breach. What data was compromised? Which parts of your site are affected?
- Isolate the Breach: Temporarily take impacted areas offline to prevent further damage.
- Change Credentials: Update passwords for all accounts, especially for admins and sensitive user data.
Once you’ve managed the immediate threat, it’s crucial to communicate transparently with your users. Inform them of the breach, how it occurred, and the steps you are taking to address it. This not only builds trust but also keeps users alert to any suspicious activity on their accounts.
Enhancing Security Post-Breach: After containment, focus on strengthening your site’s security to prevent future incidents:
- Update Software: Ensure all plugins, themes, and WordPress core files are up-to-date.
- Install Security Plugins: Utilize reputable security plugins that offer firewalls, malware scanning, and login protection.
- Regular Backups: Implement a routine backup schedule, ensuring you can restore your site to a safe version if necessary.
Consider creating a comprehensive cybersecurity policy that outlines your response plan for future breaches. This policy should include regular security audits and staff training to recognize potential threats. Engaging with a cybersecurity professional can also be invaluable. Experts can help you assess vulnerabilities and establish a fortified security posture.
| Action Item | Frequency |
|---|---|
| Security Audits | Quarterly |
| Software Updates | Monthly |
| User Training | Bi-Annually |
Ultimately, a proactive approach is your best defense against cyber threats. By understanding the risks and committing to ongoing security practices, you transform your WordPress site into a robust fortress against potential breaches.

The Future of WordPress Security: Embracing Innovative Solutions
Innovative Solutions for a Secure Future
As cyber threats continue to evolve, WordPress site owners must adopt a proactive stance toward security. By embracing cutting-edge technologies and strategies, you can significantly enhance your site’s defenses against potential attacks. Here are some key innovations to consider:
- Artificial Intelligence (AI) and Machine Learning: Implement AI-driven plugins that analyze user behavior, detect anomalies, and automatically respond to suspicious activities. This allows for real-time threat identification and mitigation.
- Web Application Firewalls (WAF): Utilize advanced WAF solutions specifically designed for WordPress. These firewalls can filter out malicious traffic before it reaches your site, providing an essential layer of security.
- Regular Security Audits: Conduct routine security audits using automated tools that identify vulnerabilities. Prioritize patches and fixes to keep your website fortified against new threats.
- Multi-Factor Authentication (MFA): Encourage the use of MFA for all user logins. This simple yet powerful addition can drastically reduce the risk of unauthorized access.
Building a Secure Ecosystem
Incorporating these advanced solutions is only part of the equation. Creating a culture of security within your team is equally vital. Consider the following practices:
- Continuous Education: Regularly train your team on the latest security threats and best practices. Awareness is the first line of defense.
- Collaborative Approach: Foster collaboration between developers, content creators, and security experts to ensure that security considerations are integrated into the entire development process.
- Community Engagement: Leverage the wealth of knowledge within the WordPress community. Participate in forums and discussions to stay informed about the latest security trends.
Investment in Security: A Necessity
Investing in innovative security solutions is crucial for the longevity of your WordPress site. The cost of recovering from a security breach often far exceeds the expenses of preventative measures. Here is a simplified comparison:
| Investment | Estimated Cost |
|---|---|
| Regular security updates | $$$ |
| AI-driven security plugins | $$$ |
| Post-breach recovery | $$$$$ |
By prioritizing security and harnessing innovative solutions, you can not only protect your WordPress site but also build a resilient digital presence that inspires trust among your users. The future of WordPress security lies in our ability to adapt, evolve, and proactively safeguard our assets in an ever-changing landscape.
Taking Control: Building a Proactive Security Culture for WordPress Users
In an era where cyber threats are omnipresent, fostering a proactive security culture among WordPress users is more crucial than ever. By cultivating a mindset that prioritizes security, site owners and administrators can not only protect their assets but also inspire their communities to follow suit. This begins with a fundamental understanding of the common vulnerabilities that can affect WordPress sites and the proactive measures that can be adopted to mitigate these risks.
Security starts with awareness. Educating yourself and your team about the most prevalent threats is the first step to building a secure environment. Consider the following common vulnerabilities:
- Plugin Vulnerabilities: Outdated or poorly coded plugins can serve as gateways for hackers.
- Weak Passwords: Simple passwords are easy targets for brute force attacks.
- Insecure Themes: Themes that are not regularly updated can harbor vulnerabilities.
- SQL Injection Attacks: Attackers can manipulate SQL queries to gain unauthorized access to your database.
To combat these threats, it is essential to implement a robust security protocol. Here are several proactive steps that WordPress users can take:
- Regular Updates: Ensure that your WordPress core, themes, and plugins are up-to-date to patch any security vulnerabilities.
- Strong Password Policies: Enforce strong password requirements and encourage the use of password managers.
- Two-Factor Authentication (2FA): Implement 2FA for an additional layer of security during login.
- Backup Solutions: Regularly back up your website data to restore it quickly in the event of an attack.
Another aspect of cultivating a proactive security culture is establishing a security team or designating a security champion within your organization. This individual can oversee security practices, conduct regular audits, and ensure that everyone is adequately trained in security best practices. A dedicated approach can foster a sense of ownership and responsibility across the team.
| Security Measure | Benefits |
|---|---|
| Regular Updates | Minimizes exploitation opportunities. |
| Strong Passwords | Prevents unauthorized access. |
| Two-Factor Authentication | Adds an extra layer of security. |
| Regular Backups | Ensures data recovery options. |
Moreover, fostering a culture of security involves open communication and collaboration. Encourage your team members to share any concerns or observations regarding potential vulnerabilities. Host regular workshops or training sessions to keep security top-of-mind and to create a community where everyone feels empowered to contribute to the security efforts.
Ultimately, building a proactive security culture is not just about implementing specific measures—it’s about instilling a mindset of vigilance and responsibility. By taking these steps, WordPress users can transform their security practices into a collective strength, creating a safer environment for everyone involved.
Frequently Asked Questions (FAQ)
Q&A: Cybersecurity Threats That Target WordPress Sites
Q1: Why should I be concerned about cybersecurity threats targeting my WordPress site?
A1: In today’s digital landscape, WordPress powers over 40% of all websites. This immense popularity makes it a prime target for cybercriminals. By understanding the threats, you empower yourself to protect not just your website, but also your reputation and your customers’ trust. Every minute you take to fortify your site is a step towards safeguarding your online presence and ensuring your hard work doesn’t go to waste.
Q2: What are the most common cybersecurity threats to WordPress sites?
A2: Some of the most prevalent threats include malware infections, brute force attacks, SQL injection, and outdated plugins or themes. Each of these vulnerabilities can lead to devastating consequences, from loss of data to compromised user information. But don’t be discouraged! Recognizing these threats is the first step towards a robust defense.
Q3: How can I tell if my WordPress site has been compromised?
A3: Signs of compromise can include unexpected changes in your website’s content, unusual user activity, a sudden drop in traffic, or alerts from your hosting provider. If you suspect a breach, act swiftly to assess the damage and start the recovery process. Remember, early detection is key to minimizing impact!
Q4: What proactive measures can I take to protect my WordPress site?
A4: Start with the basics: keep your WordPress core, themes, and plugins updated. Implement strong, unique passwords and consider using two-factor authentication. Regular backups of your site can be a lifesaver in the event of an attack. Additionally, investing in a reputable security plugin can provide layers of protection. By taking these proactive steps, you not only defend your site but also cultivate a culture of security awareness.
Q5: Are there specific plugins or tools you recommend for enhancing security?
A5: Absolutely! Popular plugins like Wordfence, Sucuri Security, and iThemes Security offer comprehensive solutions for monitoring and protecting your site. They can help with firewall protection, malware scanning, and login security. By integrating these tools, you’re not just defending your site; you’re showing your visitors that you prioritize their safety, which can build trust and loyalty.
Q6: How often should I review my site’s security?
A6: Security should never be a one-time task; it’s an ongoing commitment. Regularly review your site’s security settings, ideally on a monthly basis. Conduct security audits, update software, and monitor user activity to stay ahead of potential threats. Just as a gardener tends to their plants, nurturing your website’s security will help it flourish.
Q7: What should I do if my WordPress site gets hacked?
A7: If your site is hacked, act immediately. Change passwords, restore from backups, and scan for malware. Reach out to your hosting provider for assistance. While it’s a daunting process, remember that every challenge is an opportunity to learn and grow stronger. Recovering from a breach can lead to even greater resilience in the future.
Q8: Can I prevent all attacks on my WordPress site?
A8: While it’s impossible to guarantee complete immunity from attacks, you can significantly reduce your risk by implementing best practices and maintaining vigilance. Think of it like wearing a seatbelt; while it may not prevent every accident, it greatly enhances your safety. Stay informed, stay proactive, and maintain a positive mindset—your dedication to security will pay off.
Q9: What’s the most important takeaway regarding WordPress security?
A9: The most vital takeaway is that cybersecurity is not just a technical concern; it’s a fundamental aspect of your online identity. By prioritizing security, you’re investing in your future, your brand, and your community. Together, we can foster a safer digital environment for everyone. Embrace the challenge, take action, and inspire others to do the same!
The Conclusion
As we navigate an increasingly digital landscape, the importance of robust cybersecurity for WordPress sites cannot be overstated. The threats we’ve explored are not just numbers or abstract concepts; they represent real risks that can impact businesses, individuals, and communities. Yet, in the face of these challenges, there lies an incredible opportunity for empowerment and resilience.
By prioritizing cybersecurity measures—be it through regular updates, strong passwords, or comprehensive security plugins—you are not merely protecting your site; you are safeguarding your ideas, your work, and your potential. Each proactive step you take is a testament to your commitment to creating a secure and thriving online presence.
Remember, the journey towards a secure WordPress site is not a solitary one. Join a community of like-minded individuals who share your vision of a safer internet. Together, we can build a fortress against cyber threats, ensuring that our platforms remain safe havens for creativity, innovation, and connection.
So, let us rise to the challenge! Equip yourself with knowledge, embrace best practices, and champion the cause of cybersecurity. The future of your WordPress site—and indeed, the broader web—depends on it. Let’s protect what matters and inspire others to do the same. Your vigilance today is the key to a safer, more secure tomorrow.




