In today’s digital landscape, building secure software for wealth management is not just a necessity—it’s a commitment to trust. By prioritizing security, we empower clients to focus on growth, knowing their assets are protected. Let’s innovate with integrity!
Building Secure Software for Wealth Management
In an era where digital innovation reigns supreme, the wealth management sector stands at the forefront of a technological transformation. As we navigate this dynamic landscape, the importance of building secure software cannot be overstated. Clients entrust their financial futures to us, and with that trust comes the profound responsibility to ensure their sensitive data is safeguarded against the ever-evolving threats of cybercrime.
Imagine a world where financial advisors leverage cutting-edge technology while providing absolute peace of mind to their clients. Picture a robust financial ecosystem where security is not an afterthought but a foundational principle guiding every line of code. By prioritizing security in software development, we not only protect our clients’ assets but also empower them to engage confidently with their financial journeys.
This article will explore the critical need for security in wealth management software, highlighting best practices, innovative strategies, and the transformative power of a secure digital environment. Together, let us inspire a future where trust and technology walk hand in hand, forging resilient relationships and fostering enduring success in wealth management. Join us as we delve into the essential steps toward building secure software that not only meets compliance standards but exceeds expectations—setting a new benchmark for excellence in our industry.
Understanding the Unique Security Challenges in Wealth Management
In the realm of wealth management, safeguarding client assets and sensitive information is paramount. As digital transformation reshapes the financial landscape, wealth management firms face a distinct set of security challenges that require innovative solutions. A proactive approach to security not only protects valuable data but also fosters client trust and reinforces the firm’s reputation.
One of the foremost challenges is the increasing sophistication of cyber threats. Wealth managers must contend with:
- Phishing Attacks: Deceptive emails can trick even the most vigilant clients into divulging sensitive information.
- Ransomware: Malicious software can lock firms out of critical systems, demanding hefty ransoms.
- Data Breaches: Unauthorized access to databases can result in the exposure of confidential financial data.
Furthermore, regulatory compliance adds another layer of complexity. Wealth management firms must navigate a labyrinth of regulations designed to protect client assets and personal information. Failing to comply can lead to severe penalties and reputational damage. Key regulations include:
| Regulation | Focus Area |
|---|---|
| GDPR | Data Protection |
| FINRA | Broker-Dealer Regulations |
| SEC | Investment Advisers |
Integrating robust security measures into software solutions is essential for mitigating these risks. Wealth management firms should prioritize the following strategies:
- Multi-Factor Authentication (MFA): Enhances security by requiring two or more verification methods.
- End-to-End Encryption: Protects data in transit and at rest, ensuring confidentiality.
- Regular Security Audits: Identify vulnerabilities and assess the effectiveness of current security protocols.
Moreover, fostering a culture of security awareness within the organization is crucial. Employees at all levels should be trained to recognize and respond to potential threats. Regular workshops and simulated phishing tests can significantly enhance overall security posture.
the security challenges faced by wealth management firms are multifaceted and evolving. By investing in secure software solutions and cultivating a proactive security culture, firms can not only protect their assets but also position themselves as trustworthy stewards of client wealth.

The Imperative of a Security-First Culture in Financial Institutions
In today’s rapidly evolving digital landscape, financial institutions are more than just custodians of wealth; they are also prime targets for cybercriminals. A security-first culture is no longer a luxury but a necessity. It shapes how organizations design, build, and deploy software, especially in wealth management, where sensitive data is at stake.
Embracing a security-first mindset begins with a commitment from the top levels of leadership. When executives actively prioritize cybersecurity as a core value, it permeates through every layer of the organization, ensuring that all employees understand their role in safeguarding client assets. This cultural shift is crucial for fostering an environment where security is integrated into every aspect of the software development lifecycle.
- Continuous Education: Regular training sessions should be in place to update staff on the latest security threats and best practices.
- Cross-Department Collaboration: Encourage teams from IT, compliance, and operations to work together to identify vulnerabilities before they become exploitable.
- Adopt Secure Coding Practices: Implement guidelines that help developers write code that is resilient against attacks.
The benefits of instilling a security-first culture extend beyond mere compliance. When clients and stakeholders see a financial institution proactively addressing vulnerabilities, it builds trust. Trust translates to loyalty and can be a significant competitive advantage. In an era where a single breach can lead to irreparable damage, every effort to protect data is not just a protective measure; it’s a market differentiator.
| Security Strategy | Expected Outcome |
|---|---|
| Implementing regular security audits | Identifying vulnerabilities before they can be exploited |
| Investing in training programs | Empowering employees to recognize and mitigate risks |
| Fostering an open communication channel | Encouraging reporting of security concerns without fear |
Building secure software for wealth management isn’t just about technical solutions; it’s about creating a holistic approach that encompasses people, processes, and technology. By embedding security into the DNA of the organization, financial institutions can not only protect themselves but also pave the way for a more secure financial future for their clients.
Leveraging Advanced Technologies for Enhanced Software Security
In the fast-evolving landscape of wealth management, the importance of software security cannot be overstated. As financial institutions increasingly rely on technology to deliver seamless services, they must also embrace advanced technologies that bolster security measures, ensuring client data remains protected against emerging threats.
One of the most effective strategies involves the integration of machine learning algorithms into security systems. By analyzing vast amounts of data in real time, these algorithms can identify unusual patterns and potential breaches before they escalate. The ability to predict and respond to threats dynamically is a game-changer for wealth management software:
- Real-time threat detection: Quick identification of anomalies allows for immediate action.
- Adaptive security measures: Systems evolve based on new threats, enhancing resilience.
- Reduced false positives: Increased accuracy leads to a more efficient response process.
Complementing machine learning, the use of blockchain technology offers transformative benefits for securing transactions and data integrity. By decentralizing data storage, blockchain minimizes vulnerabilities associated with traditional databases. Key advantages include:
- Transparency: Every transaction is recorded on a public ledger, reducing the risk of fraud.
- Immutability: Once data is entered, it cannot be altered, ensuring its integrity.
- Smart contracts: Automated agreements that execute when conditions are met, ensuring accuracy and reducing human error.
Furthermore, investing in cloud security solutions is paramount. As wealth management firms transition to cloud-based platforms, the security of data in transit and at rest must remain a priority. Incorporating features such as:
| Cloud Security Feature | Benefit |
|---|---|
| End-to-end encryption | Protects sensitive information from unauthorized access. |
| Multi-factor authentication | Enhances user verification, minimizing unauthorized access risks. |
| Regular security audits | Ensures compliance and identifies potential vulnerabilities proactively. |
Lastly, fostering a culture of cyber awareness among employees is crucial. Regular training sessions that focus on the latest security protocols can significantly reduce the risk of human error, which is often a primary cause of cyber incidents. Empowering staff with knowledge and tools enhances the overall security posture of the organization, creating a robust first line of defense.
By combining these advanced technologies and a proactive security culture, wealth management firms can not only protect their assets but also inspire trust among their clients. In an industry where reputation is paramount, investing in security is not just a necessity; it is a strategic advantage.
Conducting Comprehensive Risk Assessments for Wealth Management Solutions
In the realm of wealth management, the stakes are incredibly high. Clients entrust financial institutions with their hard-earned money, making it imperative to employ rigorous risk assessment methodologies. A comprehensive risk assessment not only safeguards assets but also enhances client trust and loyalty. By meticulously identifying and analyzing potential risks, wealth management firms can develop robust strategies that mitigate threats and pave the way for sustainable growth.
To effectively conduct risk assessments, consider adopting a multi-faceted approach that encompasses:
- Market Risk Analysis: Understanding fluctuations in market conditions and their potential impact on client portfolios.
- Operational Risk Evaluation: Identifying internal processes that could fail, leading to financial loss or regulatory penalties.
- Cybersecurity Risk Assessment: Evaluating vulnerabilities within digital platforms to protect sensitive client data from breaches.
- Regulatory Compliance Checks: Ensuring all operations align with legal requirements to avoid costly fines and reputational damage.
Each of these areas demands a tailored assessment, utilizing both qualitative and quantitative data. By leveraging advanced analytics and sophisticated modeling techniques, firms can achieve a clearer picture of the potential risks involved. This meticulous examination allows wealth managers to prioritize risks and allocate resources effectively, ensuring that the most pressing threats are addressed promptly.
Moreover, the integration of technology plays a pivotal role in modern risk assessment processes. Automated tools can help streamline data collection and analysis, making it easier to identify trends and anomalies. As an illustration, the table below demonstrates how automation can enhance risk assessment capabilities:
| Traditional Method | Automated Method |
|---|---|
| Manual data entry and analysis | Real-time data aggregation and analysis |
| Time-consuming reporting | Instant risk reporting dashboards |
| High human error rate | Consistent and accurate calculations |
In addition to leveraging technology, fostering a culture of risk awareness within the organization is crucial. Regular training sessions and workshops can empower employees at all levels to recognize and report potential risks, creating a more resilient organization. By embedding risk assessment practices into the company’s ethos, wealth management firms can not only protect their assets but also enhance their reputation in the industry.
Ultimately, conducting thorough risk assessments is not merely a compliance necessity; it is a strategic advantage. By taking proactive measures to identify and mitigate risks, wealth management firms can inspire confidence among their clients, ensuring a secure and prosperous financial future for all parties involved.
Integrating Robust Authentication Mechanisms to Protect Client Data
In the ever-evolving landscape of wealth management, safeguarding client data is paramount. As financial institutions increasingly adopt digital solutions, the need for robust authentication mechanisms becomes critical. A multi-layered authentication approach not only fortifies security but also fosters trust among clients, ensuring their sensitive information remains protected.
Implementing two-factor authentication (2FA) is one of the most effective strategies to enhance security. By requiring users to provide two different forms of identification before accessing their accounts, you significantly reduce the risk of unauthorized access. This can be achieved through:
- Something the user knows (e.g., password)
- Something the user has (e.g., smartphone app, hardware token)
Moreover, the adoption of biometric authentication is revolutionizing security measures. Utilizing fingerprints, facial recognition, or voice patterns provides an additional layer of security that is difficult to replicate. This technology not only improves user experience by streamlining access but also enhances protection against identity theft.
Regular security audits and updates are essential in maintaining strong authentication mechanisms. By routinely assessing your systems for vulnerabilities, you can preemptively address potential security threats. Consider establishing a proactive schedule for audits, which includes:
| Audit Type | Frequency | Purpose |
|---|---|---|
| Vulnerability Assessment | Quarterly | Identify potential security weaknesses |
| Penetration Testing | Biannually | Simulate attacks to test defenses |
| Compliance Checks | Annually | Ensure alignment with legal requirements |
Additionally, client education plays a vital role in creating a secure environment. Providing resources about safe online practices, such as recognizing phishing attempts and using strong passwords, empowers clients to take an active role in their security. Consider implementing:
- Informative webinars on cybersecurity best practices
- Regular newsletters featuring updates on security trends
- Interactive quizzes to reinforce learning
Ultimately, integrating these advanced authentication mechanisms not only protects client data but also positions your firm as a leader in security and innovation. By prioritizing robust authentication strategies, you not only safeguard sensitive information but also build a solid foundation of trust and reliability in your wealth management services.
Building Resilient Software Architectures Against Emerging Threats
Building Secure Software for Wealth Management
In a landscape where financial threats evolve at an unprecedented pace, crafting software architectures that are robust and adaptable is no longer optional—it’s essential. Wealth management firms must prioritize security at every stage of the development process, embedding it into the very fabric of their software solutions. This proactive approach not only protects sensitive financial data but also builds trust with clients.
To effectively combat emerging threats, consider the following key strategies:
- Implement Zero Trust Architecture: By ensuring that every user and device is authenticated and authorized, organizations can significantly reduce the risk of unauthorized access.
- Adopt Continuous Monitoring: Real-time monitoring enables teams to detect anomalies and respond to potential threats swiftly, minimizing damage.
- Utilize Secure Coding Practices: Educating developers on secure coding techniques is vital to prevent common vulnerabilities such as SQL injection and cross-site scripting.
- Regular Security Audits: Conducting frequent evaluations and penetration testing helps identify weaknesses before they can be exploited.
Furthermore, integrating modern technologies can bolster security measures. For instance:
| Technology | Benefits |
|---|---|
| Blockchain | Enhances transparency and reduces fraud. |
| Artificial Intelligence | Improves threat detection and response times. |
| Machine Learning | Identifies patterns in data and predicts potential security breaches. |
Collaboration among teams is equally crucial. Cross-functional teams—comprising developers, security experts, and business analysts—can create a culture of security awareness. Implementing DevSecOps practices ensures that security is a shared responsibility throughout the software development lifecycle, enhancing resilience against threats.
Lastly, don’t underestimate the power of user education. Regular training and awareness programs for end-users can significantly minimize risks associated with social engineering attacks. By empowering clients with knowledge, firms can transform them into the first line of defense against potential threats.
As we navigate the complexities of wealth management in the digital age, the commitment to building secure and resilient software must be unwavering. The stakes are high, and the investment in security today will pave the way for a safer and more prosperous financial future.
The Role of Regular Audits and Compliance in Software Security
In the rapidly evolving landscape of wealth management, the importance of regular audits and compliance checks cannot be overstated. These processes serve as both a safeguard and a roadmap, ensuring that organizations adhere to industry standards while also protecting sensitive financial data. By implementing a rigorous audit routine, firms can identify vulnerabilities before they become breaches, thereby fostering a culture of security that resonates throughout the organization.
Conducting regular audits allows firms to:
- Identify Weaknesses: Regular assessments help pinpoint areas of vulnerability within software systems, allowing for timely remediation.
- Enhance Accountability: Audits create a framework where employees understand their roles in maintaining security, fostering a sense of responsibility.
- Maintain Compliance: Staying updated with regulations ensures that the organization meets legal requirements, thus avoiding hefty fines and reputational damage.
- Build Client Trust: Consistently demonstrating a commitment to security reassures clients that their financial information is protected.
Moreover, compliance is not just about adhering to regulations; it’s about establishing best practices that promote a secure environment. The type of compliance relevant to wealth management includes:
| Compliance Standard | Description |
|---|---|
| GDPR | Protects personal data of EU citizens. |
| FINRA | Regulates brokerage firms and exchange markets. |
| PCI-DSS | Ensures secure handling of credit card information. |
To effectively implement these audits and compliance measures, organizations should employ a systematic approach, integrating compliance checks into their software development lifecycle. This involves:
- Regular Training: Continuous education for employees on security protocols and compliance regulations.
- Automated Tools: Utilizing software that automatically checks for compliance and security vulnerabilities regularly.
- Feedback Loops: Establishing channels for team members to report issues and suggest improvements in security practices.
Ultimately, regular audits and compliance checks are not just compliance exercises; they are integral to building resilient software that can adapt to emerging threats. Organizations that prioritize these practices are not only preparing for the unexpected but are also positioning themselves as leaders in the industry, dedicated to the security and trust of their clients. Adopting a proactive stance on security will lay the foundation for a robust and secure wealth management environment.

Fostering Collaboration Between IT and Wealth Management Teams
In today’s fast-paced financial landscape, the synergy between Information Technology (IT) and Wealth Management teams is not just beneficial—it is essential. By breaking down silos and fostering collaboration, organizations can pave the way for innovative solutions that enhance client experiences and ensure robust security in software development.
The integration of these two domains can lead to a multitude of advantages:
- Enhanced Communication: Regular interactions between IT and Wealth Management professionals can bridge gaps in understanding, ensuring that technological tools align perfectly with the financial goals of clients.
- Tailored Solutions: IT teams can develop customized software that addresses specific needs identified by Wealth Management, leading to more effective and secure financial tools.
- Proactive Risk Management: By working together, both teams can identify potential security threats early, allowing for the implementation of preventive measures before issues escalate.
Creating an environment that promotes collaboration starts with establishing clear communication channels. Regular joint meetings, workshops, and brainstorming sessions can encourage the sharing of ideas and foster a sense of teamwork. Consider implementing collaborative tools that allow both teams to share insights and feedback in real-time, ensuring everyone is on the same page.
Moreover, it is beneficial to define roles and responsibilities clearly. When team members understand their contributions to the overarching goals, they are more likely to engage actively in the collaborative process. To facilitate this, organizations can create a framework that allows for:
| Role | Responsibility |
|---|---|
| IT Team Lead | Oversee software development and ensure security standards are met. |
| Wealth Manager | Provide insights on client needs and market trends. |
| Compliance Officer | Ensure all software adheres to regulatory requirements. |
Furthermore, investing in joint training sessions can equip both teams with the necessary skills to understand each other’s domains better. For instance, IT professionals can benefit from learning about financial regulations, while Wealth Managers can gain insights into the latest technologies and data analytics. This reciprocal education fosters mutual respect and enhances teamwork.
Ultimately, is not just about improving efficiency—it’s about building a culture of innovation and responsiveness that places client satisfaction at the forefront. By working as a cohesive unit, these teams can create secure, cutting-edge software solutions that not only meet today’s demands but also anticipate future challenges in the wealth management arena.
Implementing Continuous Security Training for Development Teams
Empowering Teams with Ongoing Learning
In the ever-evolving landscape of cybersecurity, static training sessions no longer suffice. Development teams must embrace a culture of continuous security training to adapt to new threats and technologies. This approach transforms security from a checkbox activity into a core competency that enhances the overall quality of software.
By integrating continuous security training, teams can:
- Stay updated on the latest vulnerabilities and threats.
- Enhance their understanding of secure coding practices.
- Encourage proactive identification and mitigation of security risks.
- Foster collaboration between development and security teams.
An effective training program should be dynamic and incorporate various learning modalities. Consider the following strategies:
- Interactive Workshops: Host regular workshops where devs can practice real-world scenarios, enhancing their problem-solving skills.
- Online Courses: Leverage e-learning platforms to provide resources on secure coding and compliance standards, allowing for flexible learning.
- Gamification: Use gamified elements, such as security challenges and leaderboards, to motivate and engage the team in security best practices.
Moreover, to assess the effectiveness of the training, it’s crucial to implement regular evaluations. This can be facilitated through:
| Evaluation Method | Description |
|---|---|
| Quizzes | Short assessments after training sessions to reinforce learning. |
| Simulated Attacks | Conduct penetration tests to measure the team’s response to security breaches. |
| Feedback Surveys | Gather insights from team members to improve future training sessions. |
As development teams become more familiar with security protocols, they can create a resilient software environment, significantly reducing vulnerabilities. This not only enhances the software’s integrity but also builds trust with clients in the wealth management sector, where data security is paramount.
Ultimately, fostering a mindset of continuous learning empowers developers to take ownership of security, cultivating a proactive rather than reactive approach. The journey towards building secure software begins with investing in your team’s knowledge and skills, ensuring that they are not just coders, but guardians of security.
Creating User-Centric Security Features to Enhance Client Trust
In today’s digital landscape, prioritizing security is not just a necessity; it’s a commitment to your clients. Enhancing client trust begins with a thorough understanding of their concerns and creating security features that resonate with their needs. By adopting a user-centric approach, developers can create intuitive security mechanisms that not only protect sensitive data but also empower clients to feel in control of their information.
Transparent Security Measures should be at the heart of any wealth management software. Clients want to know how their data is being protected. Clear communication about security protocols builds confidence and enhances trust. Consider implementing features such as:
- Real-time notifications of account activity.
- Easy-to-understand privacy policies outlining data usage.
- Regular security updates shared with clients through newsletters or app notifications.
Incorporating multi-factor authentication (MFA) is another critical aspect of user-centric security. This additional layer of protection ensures that even if passwords are compromised, unauthorized access remains thwarted. Clients appreciate knowing that their accounts are safeguarded by innovative technologies, which can include:
- Biometric login options (e.g., fingerprint or facial recognition).
- SMS or email confirmations for transactions over a certain amount.
- Backup codes for secure access in case of lost devices.
User-Friendly Interfaces also play a vital role in enhancing security. A complicated security protocol can frustrate users and lead to disengagement. Designing interfaces that guide clients through security features ensures they can easily navigate protections. Features to consider include:
- Step-by-step onboarding tutorials for new security features.
- Visual indicators that show the security status of their accounts.
- Accessible FAQs and customer support for security-related inquiries.
| Security Feature | Client Benefit |
|---|---|
| Multi-factor Authentication | Enhanced protection against unauthorized access |
| Real-Time Alerts | Immediate awareness of account changes |
| User-Friendly Security Settings | Empowerment through easy management of security options |
Lastly, fostering an ongoing dialogue about security with clients is essential. Regular feedback sessions can help identify areas for improvement and address client concerns before they escalate. By creating a community around security, firms can cultivate a sense of partnership with their clients, which in turn reinforces trust and loyalty.
Embracing Agile Development for Rapid Security Adaptation
In the fast-paced world of wealth management, adapting swiftly to emerging security threats is not just an option; it’s a necessity. Agile development offers a transformative approach, allowing teams to respond dynamically to changes while maintaining robust security protocols. By embracing agile methodologies, organizations can enhance collaboration, increase flexibility, and ultimately deliver secure software solutions that meet the evolving needs of their clients.
At the heart of agile development is the principle of iterative progress, which encourages regular reassessment of security measures. This is crucial in wealth management, where regulatory requirements and threat landscapes are constantly shifting. Teams can implement regular feedback loops, facilitating:
- Continuous Integration and Deployment: Security updates can be integrated into the development cycle seamlessly, reducing vulnerabilities.
- Real-time Risk Assessment: Developers can assess security impacts on-the-go, allowing for immediate adjustments to the software.
- Stakeholder Collaboration: Continuous communication with clients and stakeholders ensures that security concerns are addressed promptly and effectively.
Incorporating security as a core component of the agile methodology fosters a culture of shared responsibility. By involving all team members in security discussions, organizations can create a security-first mindset. This collaboration not only strengthens the software but also builds trust with clients, assuring them that their sensitive data is safeguarded by a proactive approach.
Another significant advantage of agile development is the ability to conduct frequent security testing. Regular penetration testing and vulnerability assessments can be scheduled throughout the development process, rather than waiting until the project is near completion. This proactive stance not only uncovers issues early but also minimizes the cost and impact of potential breaches. Teams can iterate on their solutions, refining them based on test results and greater understanding of threats.
Furthermore, agile practices enable teams to stay ahead of compliance requirements. In a highly regulated space like wealth management, aligning with standards such as GDPR or FINRA can be daunting. Agile’s adaptability allows organizations to pivot quickly when new regulations emerge, ensuring that their software remains compliant without extensive rework.
| Agile Practice | Security Benefit |
|---|---|
| Sprint Retrospectives | Identify and address security gaps in past iterations. |
| Daily Stand-ups | Discuss security issues promptly with the entire team. |
| User Stories | Include security requirements as a priority in development. |
| Continuous Feedback | Integrate client security concerns into the development process. |
By adopting agile development practices, wealth management firms can not only enhance their software security but also foster a culture of innovation and resilience. This approach empowers teams to respond to threats in real time while keeping client trust firmly intact. The outcome is a secure, adaptable software solution that meets the demanding landscape of today’s financial industry.
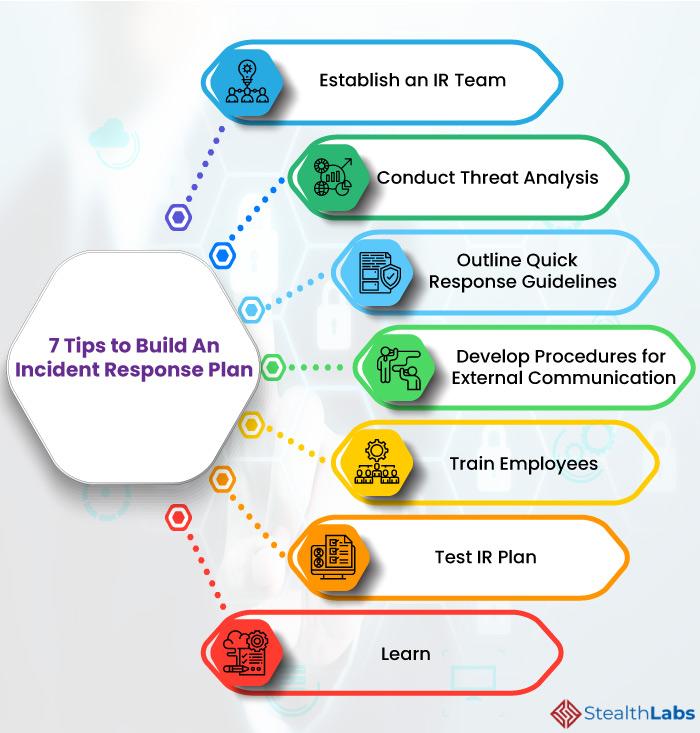
Developing Incident Response Plans for Swift Security Breaches
In the fast-paced world of wealth management, the potential for security breaches is ever-present. An effective incident response plan is not just a safeguard; it’s a lifeline that ensures your organization can respond swiftly and effectively when a breach occurs. The cornerstone of such a plan lies in its proactive measures and clear protocols that empower your team to act decisively.
To create a robust incident response plan, consider incorporating these essential elements:
- Risk Assessment: Regularly evaluate assets, vulnerabilities, and potential threats to identify high-risk areas.
- Team Roles and Responsibilities: Clearly define who is responsible for what, ensuring that every team member knows their role during an incident.
- Communication Protocols: Establish guidelines for internal and external communications, ensuring timely and accurate information dissemination.
- Response Procedures: Develop detailed procedures for identifying, containing, eradicating, and recovering from incidents.
- Training and Simulations: Regularly conduct drills to prepare your team for real-world scenarios, enhancing confidence and response time.
In addition to these foundational aspects, it’s crucial to maintain a dynamic approach. Regularly update the incident response plan to reflect new threats, technologies, and regulatory requirements. This adaptability not only ensures compliance but also strengthens your organization’s resilience against evolving cyber threats.
Furthermore, implementing a feedback loop into your incident response strategy can significantly enhance its effectiveness. After any incident, conduct a thorough post-mortem analysis to identify successes, failures, and areas for improvement. This continual learning process transforms every experience into a stepping stone for future preparedness.
| Key Components | Description | Importance |
|---|---|---|
| Incident Identification | Recognizing and categorizing the nature of the incident. | Enables swift action to contain the threat. |
| Containment Strategy | Steps to limit the damage during a breach. | Minimizes impact on operations and data. |
| Eradication Process | Removing the cause of the incident. | Essential for preventing recurrence. |
| Recovery Plan | Restoring systems to normal operations. | Ensures quick return to business as usual. |
Ultimately, an effective incident response plan is a critical component of your overall security posture. By committing to a culture of readiness and resilience, you not only protect your organization from potential breaches but also foster trust and confidence among your clients. A well-prepared team is your greatest asset in navigating the complexities of the digital landscape.

Ensuring Transparency in Security Practices to Boost Client Confidence
In today’s digital landscape, the importance of transparent security practices cannot be overstated. Clients in the wealth management sector are increasingly aware of the risks associated with data breaches and cybersecurity threats. To foster trust and confidence, companies must prioritize clarity in their security protocols. By openly communicating security measures and policies, organizations can create a culture of trust that resonates with clients.
Implementing transparent security practices involves several key elements:
- Clear Communication: Regularly update clients on security policies and the measures taken to protect their data. This could include newsletters, webinars, or dedicated sections on your website.
- Third-Party Audits: Engage independent firms to conduct security audits and share the results. This external validation reassures clients that your practices meet industry standards.
- Incident Response Plans: Clearly outline your strategy for addressing potential security incidents. Clients should know you have a plan in place and that you will keep them informed throughout the process.
Moreover, incorporating educational resources can empower clients to understand security better. Providing insights into common threats and best practices can not only enhance their awareness but also establish your firm as a knowledgeable leader in the field. Consider offering:
- Security awareness training sessions.
- Informative blog posts or articles.
- FAQs addressing common security concerns.
Using technology to bolster transparency is also essential. Implement dashboards or client portals where clients can see real-time updates on the security of their accounts. This level of visibility not only reassures clients but also encourages them to engage more actively with your services. An example of such transparency can be illustrated in the table below:
| Security Feature | Description | Client Benefit |
|---|---|---|
| Two-Factor Authentication | A security process requiring two forms of verification. | Enhanced account protection. |
| Encrypted Data Storage | Data is secured through encryption techniques. | Protection against unauthorized access. |
| Regular Security Updates | Frequent updates to address new vulnerabilities. | Staying ahead of threats. |
Ultimately, fostering transparency in security practices is not just about compliance; it is a vital strategy for building lasting relationships with clients. When clients feel confident in how their data is being managed, they are more likely to engage with your services, leading to increased satisfaction and loyalty. Embrace transparency as a core value, and watch your client relationships flourish.
Innovating for the Future: The Next Generation of Secure Wealth Management Software
As the financial landscape evolves, so does the need for innovative solutions that prioritize security and efficiency. In the realm of wealth management, where trust is paramount, the next generation of software must leverage cutting-edge technologies while ensuring robust data protection. This is not merely about keeping up with trends; it is about setting new standards that inspire confidence in clients and stakeholders alike.
Key Features of Secure Wealth Management Software:
- Advanced Encryption: Implementing state-of-the-art encryption protocols to safeguard sensitive client information.
- Multi-Factor Authentication: Utilizing multiple layers of security to verify user identities and access credentials.
- Real-Time Monitoring: Continuous oversight that detects and responds to suspicious activities instantaneously.
- Compliance Frameworks: Adhering to the latest regulations and standards to mitigate risks and enhance trust.
In the digital age, clients expect more than just traditional investment strategies; they demand personalized experiences that cater to their unique financial goals. Integrating artificial intelligence and machine learning into wealth management software can significantly refine client interactions. By analyzing vast amounts of data, these technologies can provide tailored recommendations that not only enhance user satisfaction but also optimize portfolio performance.
Benefits of Next-Gen Software Solutions:
| Benefit | Description |
|---|---|
| Enhanced Security | Reduces vulnerabilities to cyber threats through advanced security measures. |
| Increased Efficiency | Streamlines processes, allowing for quicker decision-making and improved service delivery. |
| Client Empowerment | Provides clients with intuitive tools for tracking and managing their investments. |
| Scalability | Adapts to growing business needs without compromising performance. |
Moreover, as we embrace a more interconnected world, collaboration becomes essential. Developing partnerships with fintech innovators can lead to the creation of ecosystems that not only enhance security but also provide comprehensive solutions for wealth management. By fostering an environment of collaboration, firms can leverage shared insights and technologies to drive innovation further, ensuring they stay ahead in a competitive market.
Ultimately, the future of secure wealth management lies in a commitment to transparency and trust. By adopting technologies that not only enhance security but also streamline operations, firms can foster lasting relationships built on confidence. The next generation of wealth management software is not just about safeguarding assets; it’s about creating a platform where clients feel assured, informed, and empowered to achieve their financial aspirations.
Frequently Asked Questions (FAQ)
Q&A: Building Secure Software for Wealth Management
Q: Why is security particularly important in wealth management software?
A: In the wealth management sector, we handle sensitive financial information that belongs to individuals and institutions. This data is a prime target for cybercriminals who wish to exploit vulnerabilities for financial gain. Ensuring robust security measures in our software not only protects our clients’ assets but also builds trust and loyalty. When clients know that their financial data is secure, they can focus on their investments and financial goals without fear.
Q: What are the key components of secure software in this field?
A: Secure wealth management software is built on several foundational components, including data encryption, secure authentication methods, and regular security audits. Implementing multi-factor authentication ensures that only authorized users access sensitive information. Additionally, employing strong encryption algorithms safeguards data in transit and at rest, making it nearly impossible for unauthorized parties to breach our systems.
Q: How can we inspire developers to prioritize security in their software design?
A: Cultivating a security-first mindset among developers is crucial. We can inspire them by highlighting real-world examples of data breaches and their consequences, not only for firms but for individuals affected. By emphasizing the role of secure software as a protector of client trust and financial well-being, we can motivate developers to integrate security practices from the very beginning of the software development lifecycle. Workshops, training sessions, and open discussions about the importance of security can also empower developers to take ownership of their role in creating safe software.
Q: What role does regulatory compliance play in building secure wealth management software?
A: Regulatory compliance is not just a checkbox; it is a vital component of secure software development. Regulations such as GDPR and FINRA guidelines set standards for how we handle data, ensuring that we protect our clients’ rights. By embedding compliance into our software design, we not only adhere to legal requirements but also enhance our security posture. This commitment demonstrates our dedication to ethical practices and reinforces client confidence.
Q: How can we continuously improve the security of our wealth management software?
A: The digital landscape is ever-evolving, and so should our approach to security. Regularly updating our software to patch vulnerabilities, conducting penetration testing, and soliciting feedback from users are essential practices for continuous improvement. Additionally, fostering a culture of security awareness among all employees helps us stay vigilant. We must be proactive, rather than reactive, in identifying potential threats and adapting our strategies.
Q: What is the ultimate vision for secure wealth management software?
A: Our ultimate vision is to create a secure, user-friendly platform that empowers clients to manage their wealth with confidence. By harnessing the latest technologies, we can provide innovative solutions that not only meet security standards but also enhance user experience. Together, we can build a future where security is seamlessly integrated into wealth management, enabling individuals and institutions to thrive without compromising their financial safety. Let us inspire a culture of security excellence—where every line of code contributes to a safer financial journey for all.
Final Thoughts
As we navigate the complexities of wealth management in an increasingly digital landscape, the imperative for secure software solutions has never been more pronounced. The stakes are high, not just in terms of financial assets, but also in the trust that clients place in their advisors and institutions. By prioritizing robust security measures and fostering a culture of vigilance and innovation, we can safeguard not only our systems but also the dreams and aspirations of those we serve.
Investing in secure software is not merely a technical necessity; it is a commitment to integrity, resilience, and excellence. Let us embrace this challenge as an opportunity to lead with purpose and vision. By building secure software, we are not just protecting wealth; we are empowering individuals and families to achieve their financial goals with confidence.
Together, we can forge a future where security and innovation go hand in hand, creating a foundation for sustainable growth and trust in the wealth management industry. Let us rise to the occasion, inspiring others to do the same, and pave the way for a brighter, more secure tomorrow. The time to act is now—let’s build a legacy of security, one line of code at a time.




